Important Update on IBM Verse Preview Service
by Volker Weber
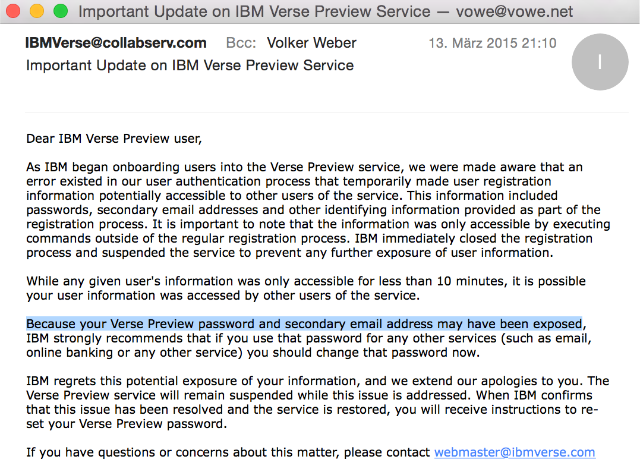
Why does IBM store my password in a way that it could be exposed? And how are you supposed to trust a cloud service with holes this size? Let's investigate what we can find out from this email:
we were made aware that an error existed in our user authentication process that temporarily made user registration information potentially accessible to other users of the service
Somebody found this hole and told IBM. The hole is in the onboarding service. That's the one that could have taken a day, remember? From the outside, this looks like IBM is taking the form with everything you enter, name, password, mail address, phone number etc. and does not safely create a directory entry where the password would be hashed. Instead this is put into a queue to be processed later, maybe somewhere else. Going out on a limb here, somebody may have found out that he could dump that queue onto his computer.
What really bothers me: I have rolled out big a$$ services myself. And there were security reviews out of the wazoo for this kind of process before you could take it live. Never in your life would you have survived with a design that stores passwords in clear text.
Does. Not. Compute.
Comments
and this is why I am glad I have switched to only using unique passwords generated by Lastpass
Not the first site to be bitten by something like this and certainly not the last
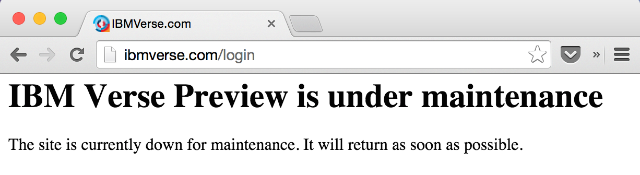
IBM tries very hard to proof that cloud services are not ready for the Enterprise. IBM Verse users cannot use the browser they want. Passwords and other sensitive data is accessable by other users. And when there is a problem the whole service will be shut down with no backup. We will stay on premise as long as it is possible.
Your Verse password is not stored in a way that could be exposed. It's stored like any other Domino HTTP password as a salted hash that has been market-tested for over a decade.
IBM was extremely responsive to the notification of the vulnerability in the registration process. Instead of getting defensive they shut down the registration service entirely, and notified registrants of a potential vulnerability which only affected a tiny fraction (about 25) of the total users.
Interesting, Nathan. IBM knows those 25 users? And why do I need to change the password elsewhere if only a salted hash exists?
It's like the pinnacle of incompetence.
I don't know whether they've identified the fraction. They could have. And they probably could have just notified that fraction, but they chose to apply the notification broadly instead.
Verse itself only has salted password hashes, but the preview registration process is not the same as Verse itself. (From an implementation standpoint, at least. I realize they're perceived by the customer as one.)
"Verse itself only has salted password hashes, but the preview registration process is not the same as Verse itself." - That reads as either "the registration process is unknown" or "the registration process does not use salted password hashes". To get from "not salted password hashes" to "salted password hashes" you need to store the password in clear text. Uggh.
If about 25 people were affected in those 10 minutes, that's only 150 per hour. Looks awfully slow. It would take 3333333 hours or 380 years to get to 500 million.
In order for Verse to gain market share, it has to come roaring out of the blocks, grab market attention and share, and be demonstrably much better than whats out there. And at no point whatsoever have a security scare like this.
It's odd - the IBM I knew a few years ago did implementations like this all the time. Now this 'new' downsized and outsourced IBM doesn't even have a decent Information Assurance audit to catch schoolboy errors like this before they come down from the whiteboard.
So if IBM can't deliver complex projects in a secure, stable and repeatable way, what *can* it do? Have they really sacked *all* the good people?
---* Bill
Well, Google seems to have bigger holes these days: http://arstechnica.com/security/2015/03/epic-google-snafu-leaks-hidden-whois-data-for-280000-domains/
IBM is joking with us. And it is not 1st of April yet. Most of the comments express surprise that IBM let something like this, but I am not. For about 2 years IBM are teasing us with this "entirely new way of work". And after all the demos, design reviews and all the talking - they delivered what?!
From my perspective this Verse preview site is something which a team of two developers can bring to life for a month. There is no surprise than that no one reviewed and tested for security issues before launch.
I do not like big software teams, but you can not launch public service like this with a team of two.
Repeating myself: They know how to shoot their feet...
Did they send this notification from IBMVerse@collabserv.com, as a blind copy, with please reply to webmaster@ibmverse.com??? That's exceptional for a professional mail service.
Maybe they can just ask some advise to the identity division?
(also this unit is not going too well and changed name several times, but there still work quite relevant people :))
http://www-03.ibm.com/software/products/en/category/identity-access-management

