Simply explained :: Do VPNs enhance your privacy?
by Volker Weber
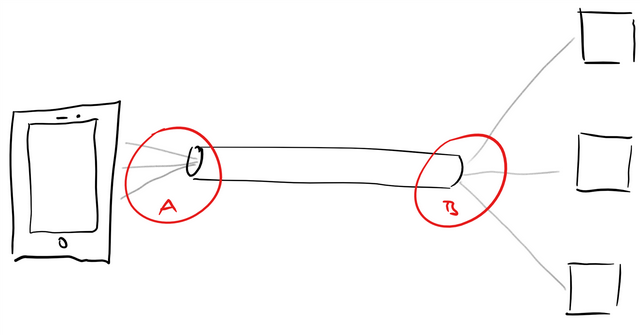
Ars Technica has a trending story about a research paper investigating hundreds of VPN apps for Android. This seems to be complicated but it isn't. It's all about a simple question: whom do you trust?
The sketch shows you how a VPN works. You have a network tunnel from point A to point B. This tunnel traverses a network you do not trust, like "The Internet" for instance. The tunnel has two endpoints A and B. They are supposed to be in safe territory. B could be behind your company firewall, A on your trusted device. Do you see the problem? A and B have to be trusted. If you have an app on A you cannot trust, or if you simply don't know where B is, then you are not enhancing your privacy because all of your traffic goes in and comes out at A and B. It is way easier to track you, if you always take the same road.
Comments
I use a VPN service mostly on open Hotel networks ... sure someone could start a MitM attack and also get my traffic but that is way more unlikely than someone just sniffing all open communication. But I do pay for my VPN service, that's why I trust them. And I do recognize that at B my traffic will also be very likely automatically analyzed by our three lettere friends.
If you want to enhance security for a particular tasks it is strongly advisable that the app that has to perform that secure transaction, is also responsible to create a trustworthy encryption.
Thanks for pointing out that a VPN only helps you to mitigate an untrusted networking segment.
You're showing off, doodling on your Surface again, aren't you vowe? :)
I wouldn't call it showing off. But you are right, that is what I use the pen for very often. I like these sketches more than Visio graphs.

