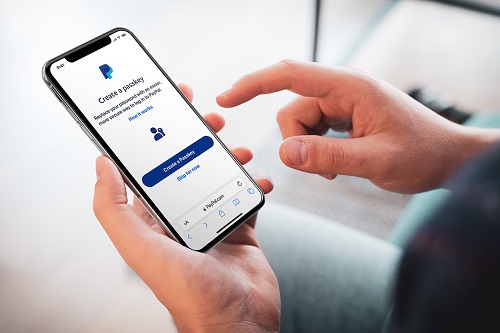
PayPal gibt Kund:innen beim Einkaufen und Bezahlen ein sicheres Gefühl, da Privatsphäre, Geld und Einkäufe bei jedem Schritt geschützt werden. Vor kurzem haben wir Passkeys für Apple– und Google-Android-Geräte als neue, einfache und sichere Anmeldemethode für berechtigte PayPal-Kund:innen in den USA eingeführt. Ab heute führen wir Passkeys auch für berechtigte Kund:innen auf Apple-Geräten und Google Android-Geräten in Deutschland ein.
Quelle: Pressemitteilung

