Microsoft is pushing the New Outlook app to Windows 11. It is replacing the old Mail & Calendar apps. However, I am unable to use this app with my Outlook.com account. And so do many others.
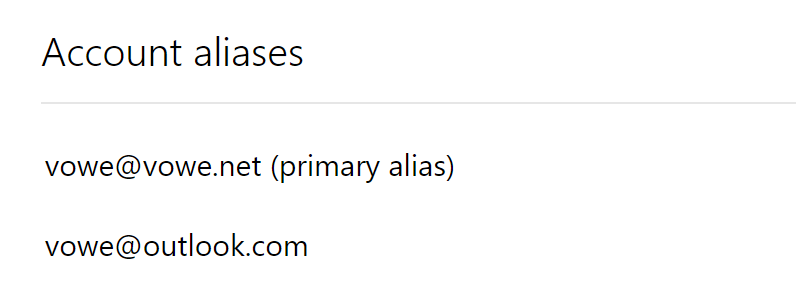
I have narrowed down the problem to a simple root cause: if you have set your personal mail address as your primary alias, you cannot add your Outlook.com account to New Outlook. If fails with both your personal email address and your Outlook.com address.
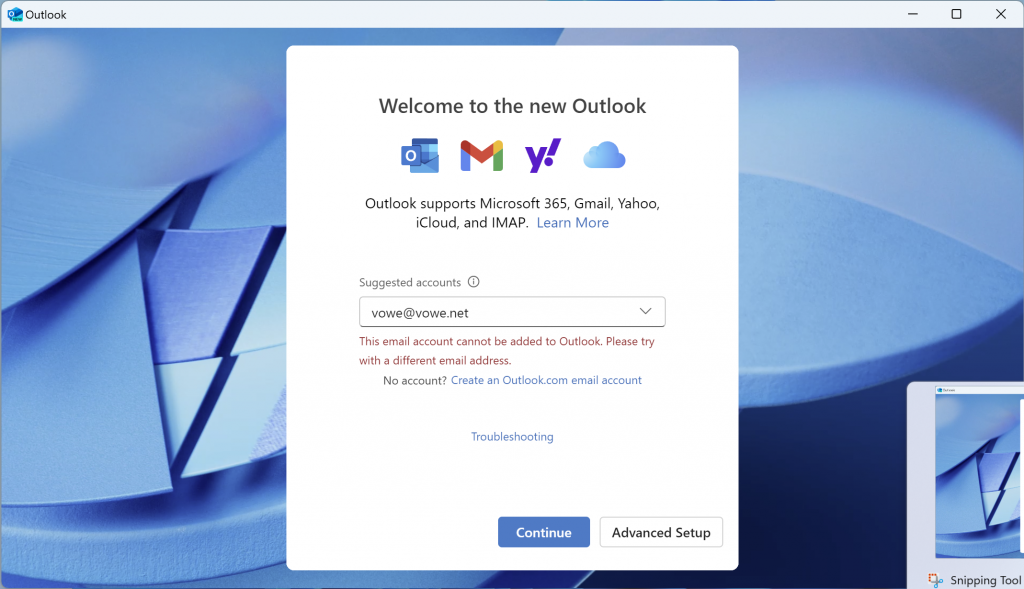
Only if you set your Outlook.com address as your primary alias, you will be able to add the account, but after that you cannot send mail from your personal email alias. Catch 22. Be extra careful when you do change your primany alias. You can only do that twice a week.
This bug is only in New Outlook and it only affects Outlook.com accounts. You can use Gmail accounts just fine. And you can use your personal email as primary alias in all other Microsoft apps, including Outlook on iOS and Outlook on Android, and the Outlook.com PWA.
I think it is quite hilarious that Microsoft only fails with the combination Windows + Outlook + Outlook.com. Let’s have a good laugh and then fix it.

